Audit findings reveal cybersecurity vulnerabilities across drilling rigs
Lessons can be learned from findings related to use of obsolete operating systems, lack of anti-malware software and security monitoring systems not being used
By Austin Hay, Stewart Gillies and Walter Knur, Aberdeen Drilling Consultants
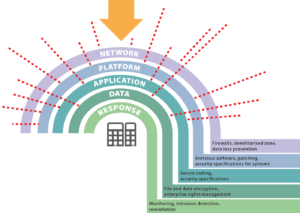
The cybersecurity threat to industrial control systems (ICS) is increasing exponentially as technologies develop and systems become increasingly connected, and the lines between information technologies (IT) and operational technologies (OT) become less distinct.
This article presents the findings of a sample of cybersecurity audits conducted by Aberdeen Drilling Consultants on ICS for typical rigs based on type, complexity and age. The aims of the audits were to:
• Evaluate the drilling contractor’s conformance to operator cybersecurity guidelines.
• Assess rig infrastructure for compliance with best practice guidelines.
The audits comprised documentation review, visual inspection of equipment and interviews with rig crew and typically followed checklists based on layered defense and the following basic cybersecurity premises: network architecture, firewall management, security monitoring, system and USB hardening, remote access, anti-malware, system security updates, backup and restore, business continuity and incident management planning, and training.
Due to the sensitive nature of the topic, the findings, while factual, have been made generic to protect the various stakeholders. The example rig reports reviewed in this article were selected based on them being examples of different rig types with typical cybersecurity features commensurate with their age and complexity. The rigs selected comprised the following:
- Advanced land rig, built 2008
- Electronic drilling controls
- Sixth-generation drillship, built 2008
- Automated drilling controls, dual derrick, vessel management systems, dynamic positioning systems, DP3
- Advanced jackup, built 2012
- Automated drilling controls, vessel management systems
- Sixth-generation semisubmersible, built 2013
- Automated drilling controls, dual derrick, vessel management systems, dynamic positioning Systems, DP3
- Seventh-generation drillship, built 2014,
- Automated drilling controls, dual derrick, vessel management systems, dynamic positioning systems, DP3
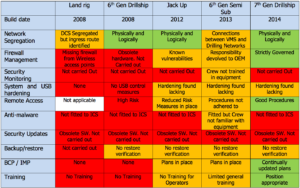
Figure 2 summarizes the findings. From this table, various patterns emerge.
- While six years between construction dates appear to be a narrow window, a comparison between the sixth- and seventh-generation drillships shows that the equipment manufacturers and drilling contractors have been considering the cyber-threat during the seventh-generation drillship build period.
- The 2013 sixth-generation semisubmersible shows an example where the drilling contractor cybersecurity training and awareness has not kept pace with OEM cybersecurity technological advances.
- Two consistent findings across the table were:
- Security updates: Because of the lead time required to build rigs and the complex control systems involved, the software is frozen early in the construction process. Because of this, they were typically built on systems such as Windows XP, which are now considered obsolete and are no longer supported by security updates. This means that they have known vulnerabilities and are reliant upon other system hardening measures for protection.
- Backup and restore: It was found that most drilling contractors have software backup procedures and software management processes in place. However, while backups were routinely taken, it was found that the restore process was never exercised, meaning that the storage media and restore processes were never validated.
- From 2008 to 2014, it can be seen that there is a transition from no protective measures being in place to a recognition and implementation of cybersecurity technologies and guidelines. Unsurprisingly, in general, it was found that the more modern the rig, the more cybersecurity features were installed.
Further findings include:
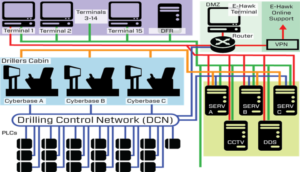
1. Network segregation – Network segregation is required to prevent malware from being communicated across networks and systems. The most modern rigs had segregated networks and utilized features such as firewalls and data diodes for one-way data transmission between networks. In all cases, office IT networks were found to be segregated from OT networks. Some network connections between various OT networks including vessel management systems, drilling systems, power management systems, CCTV systems and BOP controls systems were identified.
OEMs were found to provide network drawings for their own systems, but there were no overall vessel-specific drawings showing the areas of network interconnection between multiple vendors or the data flow logic. Understanding these interconnection areas would assist the development of plans for appropriate network segregation.
2. Firewall management – Various issues were identified with firewall management, ranging from there being no firewalls in required areas to obsolete hardware with known vulnerabilities being fitted. There was a general lack of knowledge and ownership of firewalls, ranging from obsolescence to a lack of defined rule sets. The most common finding was that firewall systems had generally not been updated since installation, and there were no management plans for firewalls, their maintenance or update.
3. Security monitoring – Only the most modern rigs had the capability to conduct security monitoring, and this was available only on certain networks. However, it was found that, while the physical capability existed, the systems were not monitored because the crews had not been trained in how to utilize the systems provided. The checking of security monitoring systems was not part of any maintenance system reviewed.
4. Anti-malware – Anti-malware software and updates were generally found only on the remote diagnostics systems. Very few other control systems were found to be fitted with anti-malware software.
5. System and USB hardening – The most prevalent operating system on the automated systems inspected was Windows XP, now considered obsolete and no longer supported by the OEM to provide security updates. This software has known documented vulnerabilities and requires protection by other system hardening measures to prevent infection.
It was also identified that system security updates were not being carried out on any of the automated systems audited. This was partly due to obsolete operating systems, but even on more modern systems, there was no methodology in place to deliver the updates. Physical system hardening by the use of USB port blockers was generally observed to be carried out. USB sticks were generally not permitted to be inserted into control systems but, where required, were generally virus-scanned prior to insertion. The most modern systems implemented various hardening measures as standard as follows:
- Operator station full-screen mode cannot close/minimize the application;
- Read access from USB devices was blocked, and USB auto-run was disabled;
- Windows explorer shell was removed, including windows taskbar and icons;
- Windows key shortcuts that may close or alter running applications were blocked; and
- Access to task manager was password-protected.
It was found in many cases that the system passwords had not been changed from default settings. This was considered poor basic cybersecurity practice.
6. Remote access – Remote access was typically used by the OEMs to diagnose equipment and software issues by utilizing an internet connection to an onboard remote diagnostics computer. The main remote diagnostics connections were for drilling control systems, vessel management and dynamic positioning systems.
Most drilling contractors had policies relating to the remote access connection to the rig. However, because the responsibility for remote access provision was for the most part devolved to the OEM by the drilling contractor, these policies were not always found to be adhered to.
ADC found instances where the OEM could directly access the rig’s systems without any approval from the rig, due to remote access system settings. Remote access was often found not to comply with recognized cybersecurity guidance in relation to the following:
- Remote access did not require two factor authentication;
- Modification to the system was possible during a remote access session;
- There were no individual accounts for remote access;
- There was no control of the user access; and
- Some computers used for remote access did not have anti-malware software installed.
7. System Security Updates – Security updates were generally found only on the remote diagnostics systems. Updates were generally stated to be provided by the OEM, but no records were found of this being recorded on any maintenance system.
The most common finding was that firewall systems had generally not been updated since installation.
On most systems inspected, security updates were not up to the latest versions. Few control systems were found to be routinely provided with security updates. As stated, the most prevalent system on the automated systems inspected was Windows XP SP3, now considered an obsolete operating system and no longer supported by the OEM to provide security updates.
8. Backup and restore – It was generally found that drilling contractors held up-to-date backups of the control system software and had a software management of change process. However, the restore process was rarely found to be carried out and, therefore, the validity of the backups was never tested.
9. Business continuity plans (BCPs) and incident management plans (IMPs) – Only the largest major companies had BCPs and IMPs in place that related to a cyber-attack or a malware event.
10. Training – Typically, IT personnel and electronic technicians were trained in basic cybersecurity. This was not always a requirement on a rig training matrix and, in general, it was found that operators were not trained in the basics of cybersecurity.
In general, it was found that the more complex the rig, the greater the managerial awareness of cyber-threats and the more policies and procedures that were in existence. However, even in the most diligent and highly regarded companies, the stated policies and procedures were not always followed. Examples of this were found in the following:
- The requirements of the policies were taken from best practice guidelines that were not technically feasible with the equipment fitted to the rig. There was no verification within the company that the policies were being adhered to. An example of this was a policy that stated that logging and monitoring was to be conducted on certain systems where there was no equipment fitted to do this.
- There was a lack of awareness of equipment obsolescence in relation to cybersecurity, particularly relating to operating systems and firewalls.
- Responsibility for firewall management was found to be devolved to the major equipment manufacturers. Firewall settings were not known to the rig owners.
- Responsibility for remote connection was devolved to the major equipment manufacturers. Because settings were not verified, they were frequently found to contravene the drilling contractor’s policy on access control and cybersecurity.
- Network equipment was not set up to provide optimum security capability from the equipment fitted.
- Equipment upgrade costs could not be met during the downturn. DC




