By Linda Hsieh, Editor & Publisher
From bounty hunter to genetic engineer to salesman to tour guide, Ben Ramduny went through several childhood dreams, ambitions and life phases before finding his passion in information and cybersecurity.
His affinity for computers began when he was a young child growing up in the English town of Crewe, playing with early-model home computers like Spectrum and Amstrad in the 1980s. This interest in computers continued throughout his childhood so that, by the time he was in his 20s, he had gained enough computer knowledge on his own to get a job on the IT help desk of Fujitsu Services.
“This was 1999, when not everybody had a computer,” he recalled.
Working for Fujitsu was interesting, and Mr Ramduny liked his job. But he still felt lacking in direction, even as he was moving up in the company by earning certifications in systems like Cisco, Check Point and Juniper, and gaining experience with technical design and network solutions.
Over time, however, he came to realize that working in security was his calling. “Working with Fujitsu’s security team, I saw they tended to be the highest-performing and brightest people. They seemed to be the best of the best, and I wanted to have the same skill set as them.”
After pursuing and obtaining his certified information systems security professional (CISSP) qualification in 2008, Mr Ramduny joined Atos Origin, an IT services corporation, as Technical Security Consultant. Immediately, he was placed on the 2012 London Olympics security project, a flagship account for the company. “It was a chance to work with people in the pinnacle of their careers,” he said.

When that project ended, Mr Ramduny was recruited away by KPMG, where he still worked in security but in a consultant capacity. Yet, he soon realized that his previous hands-on security experience gave him a leg up over many other consultants in the company. “I was one of a handful of people who actually had deep technical knowledge and could talk to a chief technology officer and give him insight that he couldn’t get from another team.”
Projects that Mr Ramduny undertook during his time with KPMG included certifying network security for the likes of British Telecom and developing the University of Manchester’s cybersecurity strategy.
His tenure at KPMG also included a two-year secondment to Shell, where he got his first taste of the oil and gas industry. As Information Risk Management Mobility Lead, his work scope included helping the operator to ensure that projects were “secure by design.”
Move Into the Drilling World
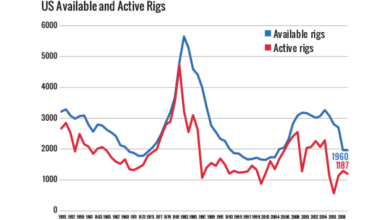
In 2015, around the time that the drilling industry started to fully recognize the need to improve its cybersecurity, Mr Ramduny joined Seadrill when the company created the new role of Information Security Manager.
“One of the first things that I did was to sit down with the CIO and walk through what security was and where we could get to, then map that to what would work for the business,” he said. Performing a cybersecurity maturity assessment was a key step.
He then helped Seadrill to develop a three-year strategy for improving its cybersecurity maturity level and build a team to deliver that strategy. “That’s really the journey we’ve been on the last few years, going from a very low maturity level of around 1 to now, where we’re at about a Level 3.” Part of achieving Level 3 means that roles, processes and controls all have to be properly documented. “It needs to be autonomous, which is to make sure that we’re not dependent on a single person.”
For a drilling company to get to this level, Mr Ramduny noted that it’s important for security professionals to talk to other people in terms that will resonate with them. “For example, firewalls are about making sure that our watertight doors stay secure on a floater. They ensure that, even if we have some water floating around, they can’t get between different compartments and destabilize the rig. We have to help them visualize the risks.”
One key challenge that remains in drilling cybersecurity, however, is to bring vendors into alignment with drilling contractors, Mr Ramduny said. Because of the expected life span of a drilling control system and the capital that would be required to invest in any new systems, drilling contractors urgently need more cost-effective technology-based security solutions that can be retrofit to existing fleets. Particularly in today’s economic environment, replacing entire drilling packages just for better cybersecurity is simply not possible.
This is an issue that Mr Ramduny hopes can be addressed by the IADC Cybersecurity Committee, where he serves as Co-Chair. By gathering drilling contractors to speak with one voice, he hopes that the message can get across to the industry’s suppliers.
“Either we get a cost-effective way to secure our systems, or the drilling contractors will do it on their own. Either way, we’re going to have to do this. Our customers are asking us to do it, and regulations in the future may well ask us to do it. It’s also just the right thing to do.” DC